Breadth & Depth
Enable your security team to run an in-depth, continuous analysis and management of your entire SaaS stack

The Ultimate SaaS Security Checklist
Get the complete checklist of SSPM & ITDR capabilities and features
Adaptive Shield can integrate with over 150 apps and contextualizes all the items at risk to help your security team prioritize the configuration weaknesses and increase time and efficiency to remediation.
Learn more
Slice and dice security checks by domain from Access Control, Password Management, MFA, to DLP, Malware Protection, Privacy Control, Auditing, Mobile Security, Endpoint Protection, Phishing Protection, Operational Resilience, Key Management and more.
Learn more
Compare your SaaS security checks with the major industry standards, such as NIST, SOC2, ISO, to ensure you comply. Or build your own custom company policy.
Learn more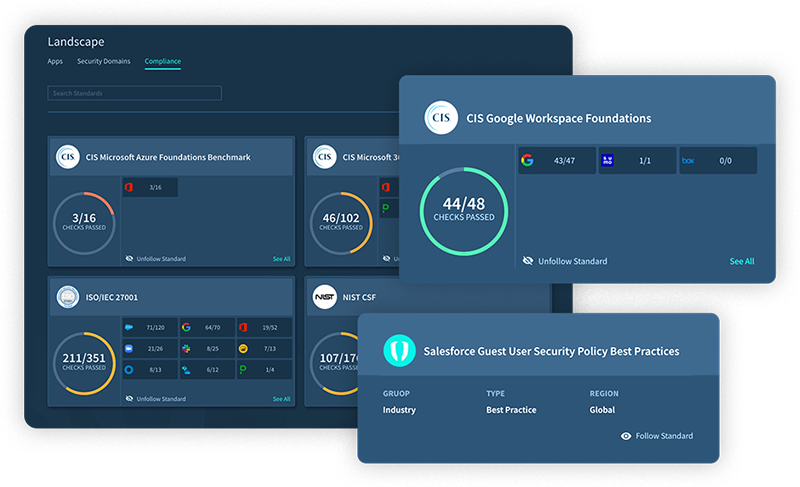
Set alerts to know immediately about any configuration drifts or potential risks.
Integrate these alerts with your company’s change control processes to enable the security team to monitor everything from a single pane of glass.
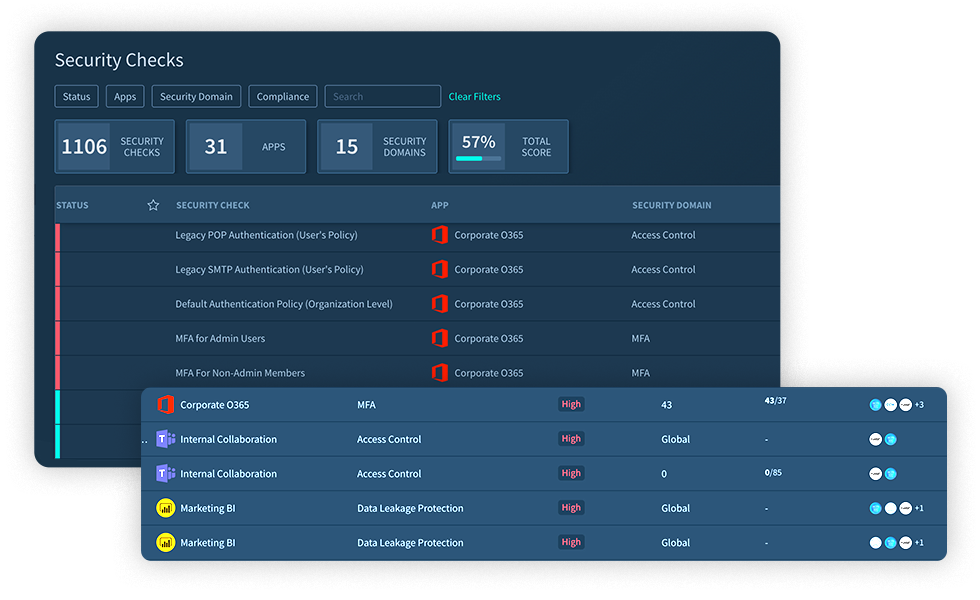
Gain full context to the security risk including extent and severity of exposure as well as stakeholders impacted.
See exactly how to fix the SaaS misconfigurations either directly from the system or easily share issues through the ticketing system of choice. You can also opt-in to a ‘Fix now’ functionality if you want Adaptive Shield to resolve these errors directly.

Gain a comprehensive view of users across all connected SaaS apps.
Attain visibility of active or deactivated SaaS app users, with insight to all the privileged roles and user-specific failed security checks. Adaptive Shield enables seamless user management and investigation across all SaaS apps, which is critical for securing sensitive users such as IT admins and executives.

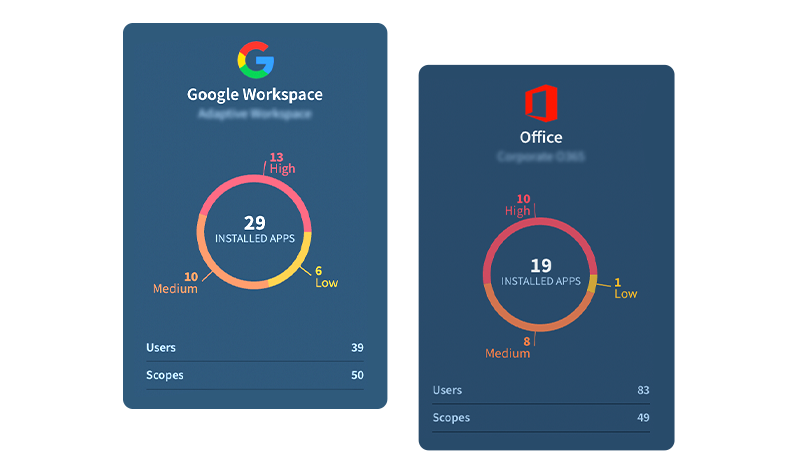
Gain visibility into 3rd-party apps integrated with your SaaS stack.
3rd-party app access is the new executable file. An innocuous process, people don’t think twice when connecting an app they need with their Google workspace or M365 environment, etc. However, this SaaS-to-SaaS communication is an emerging threat in the corporate cybersecurity landscape.
Visibility of all Shared Sensitive Information.
Gain visibility into the share settings of every document, file, and digital asset within your SaaS stack. Adaptive Shield helps identify high-privilege resources that are at risk of leaking, and protects against data exfiltration.

Correlate the risk of SaaS users and their endpoints.
Through the device inventory, you gain visibility into the devices that have access to the company’s SaaS apps and manage risks based on the device hygiene score.

See all threats facing your SaaS stack, sorted by severity, application, type, or date, together with recommended mitigation actions and each threat location on the MITRE ATT&CK framework.
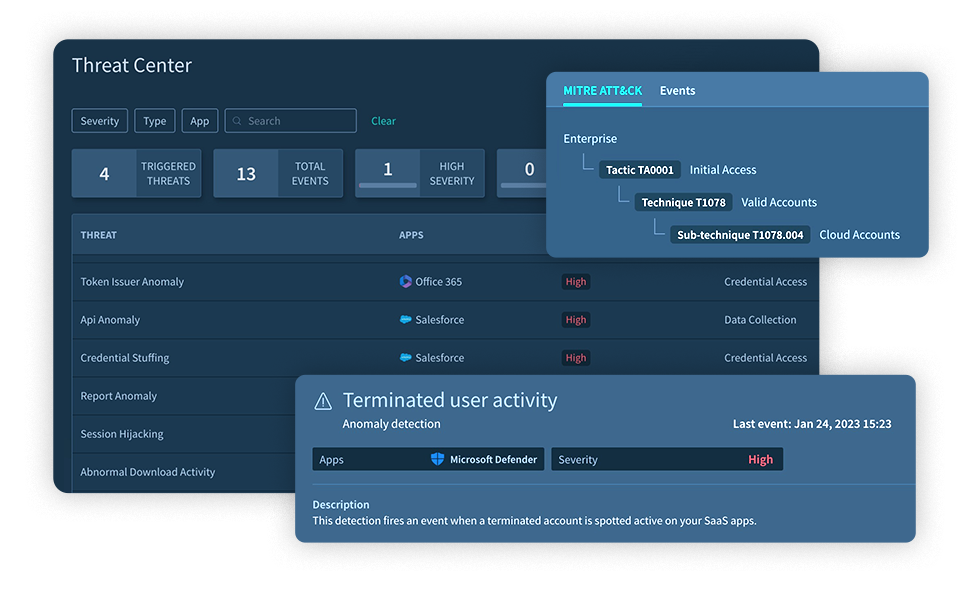
Monitor privileged users and their activities to track user behavior and detect when suspicious activity occurs.

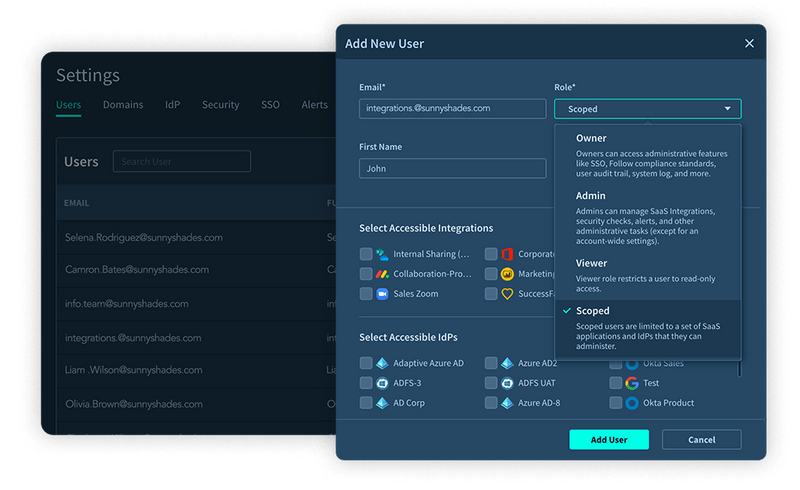
Solving the all-too-common issue SaaS app delegation — often the SaaS app owner sits outside of your security team.
Adaptive Shield offers limited access to the platform so the SaaS app owner, outside of your security team can have visibility into their owned apps and remediate issues right away, while your security team oversees.
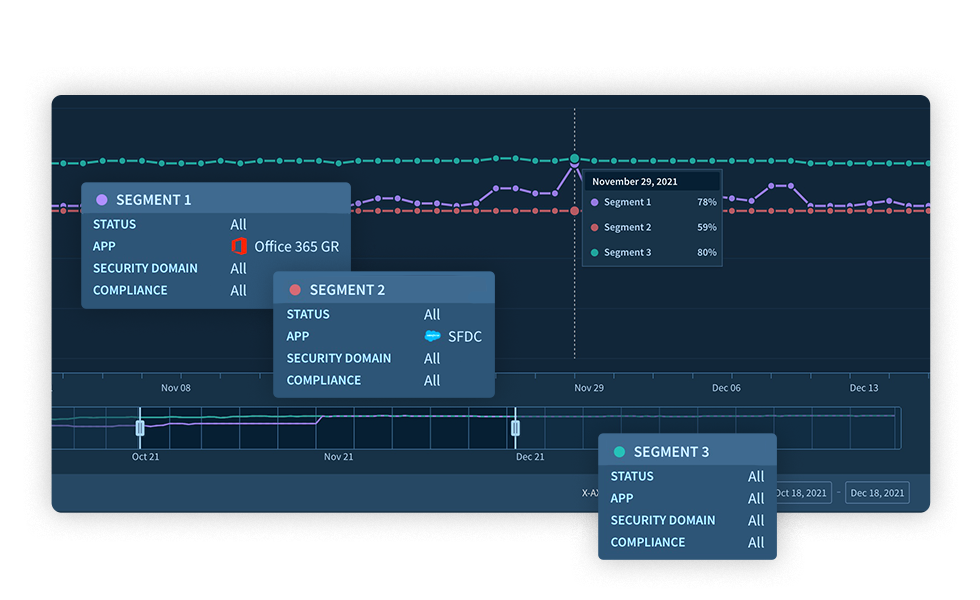
Snapshots aren’t enough to view network changes.
Get a timeline view of your SaaS environment so you can detect changes and see how your system has evolved over time.
 ?>
?>