What is CASB?
Cloud Access Security Brokers (CASB) have been around for over a decade, continually adapting to meet the needs of cloud and SaaS security. CASBs focus on applying corporate policies to cloud-based entities, and have a wide range of uses. Traditional CASBs act like a firewall, where all connectivity to SaaS applications passes through a CASB proxy server where it is monitored and all actions are approved. Next gen CASBs connect to SaaS apps through APIs, giving them more access and increasing their SaaS monitoring functionality.
CASBs enable organizations to apply policies across all corporate users, covering things like password rules, SSOs, and permissions, as well as monitoring and applying the way data moves from place to place.
How Does CASB Work with SaaS Security?
Many organizations initially used CASBs to secure their SaaS applications. The tool was adequate when organizations believed that SaaS security was limited to employee SaaS usage, offboarding, and data governance.
However, SaaS’s evolution has far outgrown CASB’s capabilities, and the limitations inherent in CASB make it unsuitable as a modern security tool. CASB solutions are unable to secure the stack for a number of reasons, including:
Limited Discovery
CASB relies on event logs, causing it to miss user-SaaS context and giving it limited visibility of SaaS apps
Prioritization Bias
CASB prioritizes observed activity from applications and the data model it supports but ignores most shadow apps
Security Blindness
CASB focuses on pathways and looking at the app “from the outside,” causing it to miss user behavior nuances
Orchestration Hurdles
CASB struggles with tracking history and unmanaged apps in the SaaS lifecycle
Lack of Adaptability
CASB lacks flexibility in addressing evolving SaaS characteristics and threats
Contrast that with SaaS Security Posture Management (SSPM) platforms, and it is easy to understand why security teams are moving away from CASBs.
SSPMs were designed to secure SaaS applications while working in partnership with application administrators. They provide far better visibility into configurations, users, and third-party apps than any other tool. SSPMs also allow organizations to respond to threats and configuration drifts to mitigate risks. They include remediation steps, alerts, and ticket creation, all of which are lacking in even the most advanced CASB solution.
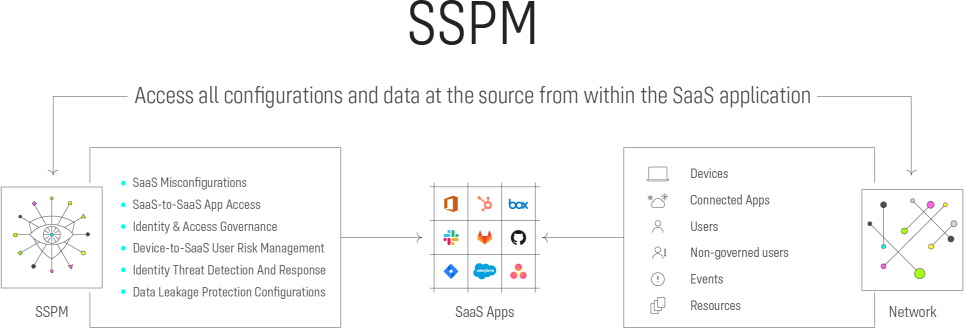
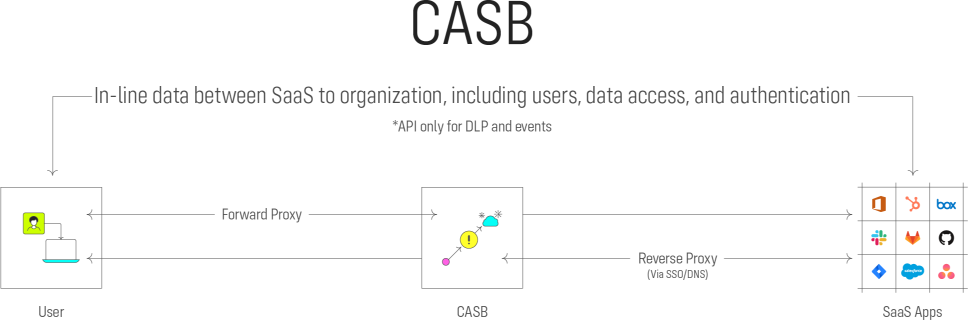
SSPMs and CASBs Complement Each Other
SSPMs and CASBs are both part of the rich cloud security fabric necessary to protect sensitive data. CASBs focus on applying corporate policies relating to identity, permissions, and encryption. SSPMs complement those efforts by protecting the data and securing access within the individual SaaS application based on usage and configuration settings.
CASBs are proxy-based solutions. They inspect traffic, as well as identify malicious activity and data exfiltration from an in-line perspective of a governed user. SSPMs extend that coverage to external users, contractors, partners, third-party applications, and IoT devices.
CASBs are effective at detecting users who access more data than they should or access data that they should not be seeing. SSPMs add additional protection by identifying misconfigurations that could lead to data becoming publicly accessible without user registration or user creation.
SSPMs are significantly less expensive than CASBs and have a far simpler setup, allowing organizations to protect their entire SaaS stack rather than just a few critical applications. Furthermore, SSPMs can identify non-IdP users that sit outside the organization, and identify user devices with poor security hygiene, capabilities that complete CASB.