What are Data Leakage and Data Leakage Protection?
Data leakage is the unauthorized transmission of data from within an organization to external destinations or parties. In a SaaS context, it can refer to data that is exposed without passwords or an expiration date. The data may contain sensitive financial records, customer PII, strategic documents, or any number of things that are best kept within the organization.
Data Leakage Protection (DLP) are the configurations within the SaaS applications that limit exposure. They make up 13% of all SaaS app configurations, protecting sensitive data in Google Workspace, Microsoft 365 (M365), Salesforce, Box, Workplace, ServiceNow, and hundreds of other applications.
Why is Data Leakage Protection challenging to enforce?
Employees often need to share documents with external stakeholders, including vendors, partners, and freelancers. To truly be secure, files should be authorized for use by specific users and include an expiration date when the file is no longer accessible. However, this can become difficult in practice.
When multiple users within a vendor need to review the document, employees must choose between clicking “share with all users” or add specific users that can access the files. For employees that aren’t security experts or concerned about security issues, sharing with anyone with the link is the preferred choice. They don’t need to add multiple users to a file or be bothered by file-sharing requests.
The trade-off for that convenience is a weakening of document security. When files don’t require passwords or login names, they can be accessed by anyone. The configurations within the SaaS application are in place to prevent this type of exposure, which is why we’re sharing some key benchmarks that companies are using for high-risk DLP configurations in Salesforce, M365, and Google Workspace.
Configurations that Matter in DLP
Monitoring files that have been shared outside the organization is a difficult task. Once files have been shared, it is almost impossible to track their distribution. The types of configurations that are most concerning from a DLP perspective center on:
- Guest Link Resharing
- External Links File Permissions
- External File and Folder Sharing
- Links Exported Outside Your Team
- Old Pending Invitations
- Shared Links Expiration
- User’s Desktop Sync
Preventing Data Leakage from Salesforce
Guest User Sharing
Salesforce relies on configurations to prevent data from being exposed to external users. When set correctly, Guest User Sharing Rules ensure that documents remain secure and that only authenticated guest users can access a file.
However, when Guest User Sharing Rules are enabled, uncredentialed users can access any document that matches the sharing rule’s criteria. In its guidelines, Salesforce tells administrators to implement security controls that match the sensitivity of the data, and reminds users that “Salesforce is not responsible for any exposure of your data to unauthenticated users based on this change from default settings.”
While there are use cases for allowing this permission, it is critical that security teams periodically review their sharing settings to protect confidential files from exposure. To check those permissions:
- Go to Setup
- Click Settings
- Click Security
- Click Sharing Settings, Sharing Rules
- Review all sharing rules that are detailed in the Security Check.
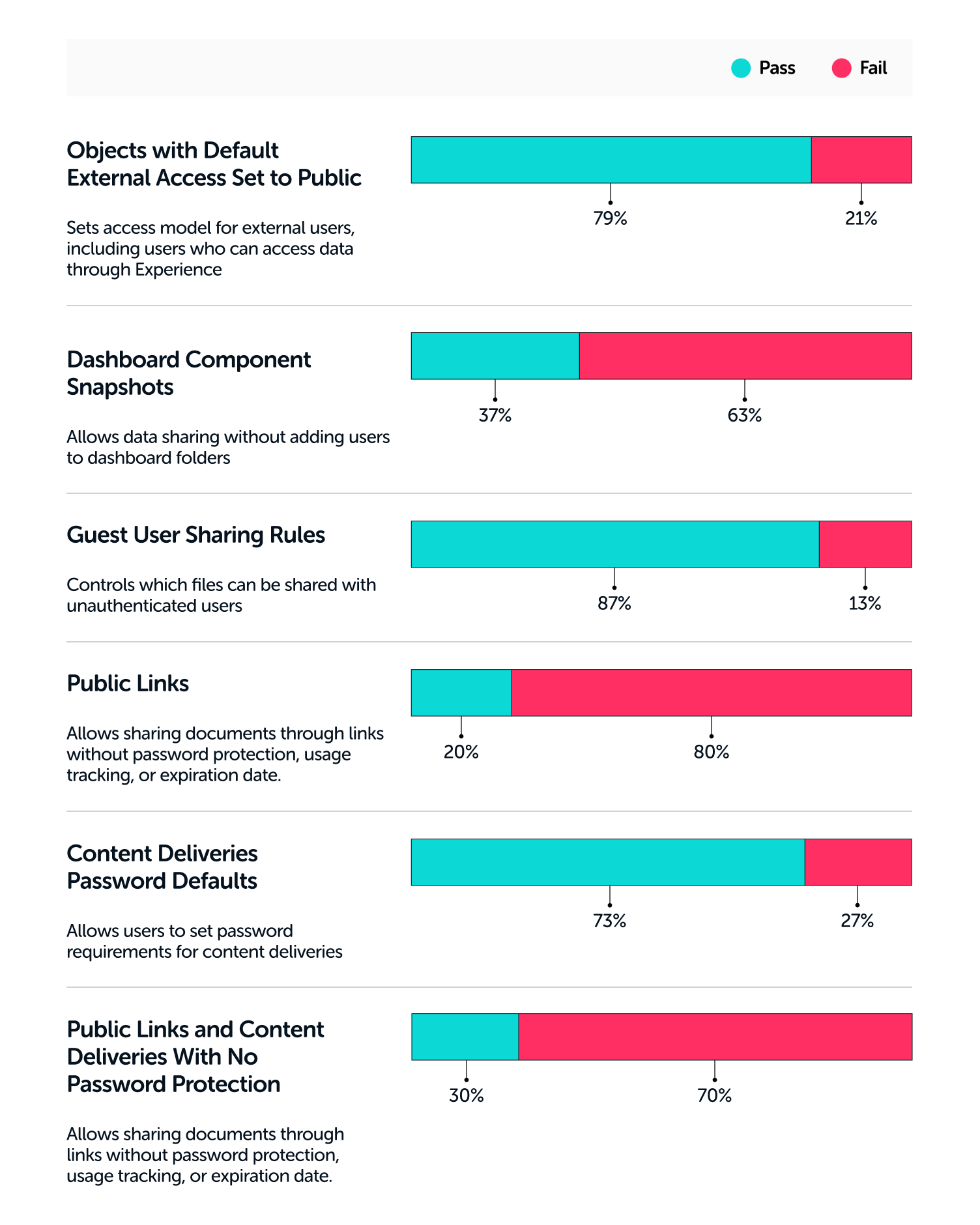
Data Leakage Benchmarks for Salesforce
Benchmark your Data Leakage Protection settings against other Salesforce users.
Securing Data in Microsoft 365
Forwarding SMTP to External Addresses
Automated email forwarding to external email addresses can pose a security risk, as confidential information and files may be shared outside the organization. Microsoft 365’s configurations enable administrators to configure inbox rules that prevent users and administrators from mailbox forwarding.
Outbound spam filter policies can be used to control automatic forwarding. By turning the setting off or selecting Automatic – System-controlled, automatic forwarding to external email addresses is disabled.
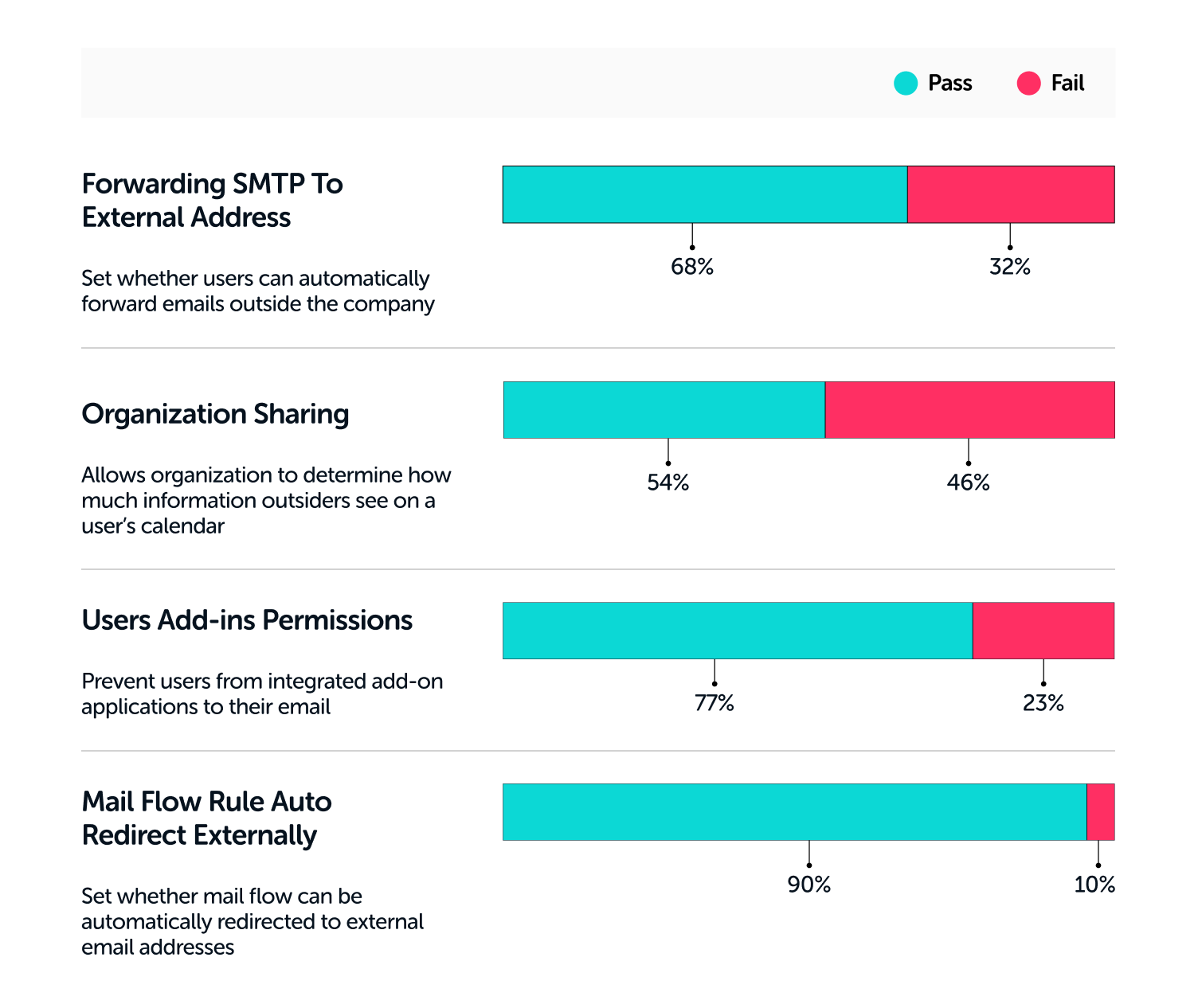
Data Leakage Benchmarks for Microsoft 365
Here are some M365 benchmarks to measure your settings against.
Preventing Data Leakage from Google Workspace
Desktop Backup and Sync
Google Workspace enables users to have desktop access to their files in Google Drive by deploying the Backup and Sync client. However, this feature stores Google files locally on the desktop, where they can be opened and read by anyone with access to the computer.
To reduce the risk of data leaks, desktop access to Drive should be removed. To do so, follow these steps:
- Go to Admin Console Home Page
- Select Apps
- Select Google Workspace
- Select Drive and Docs
- Select Features and Applications
- Select Drive
- Select “Do Not Allow Backup and Sync in your Organization
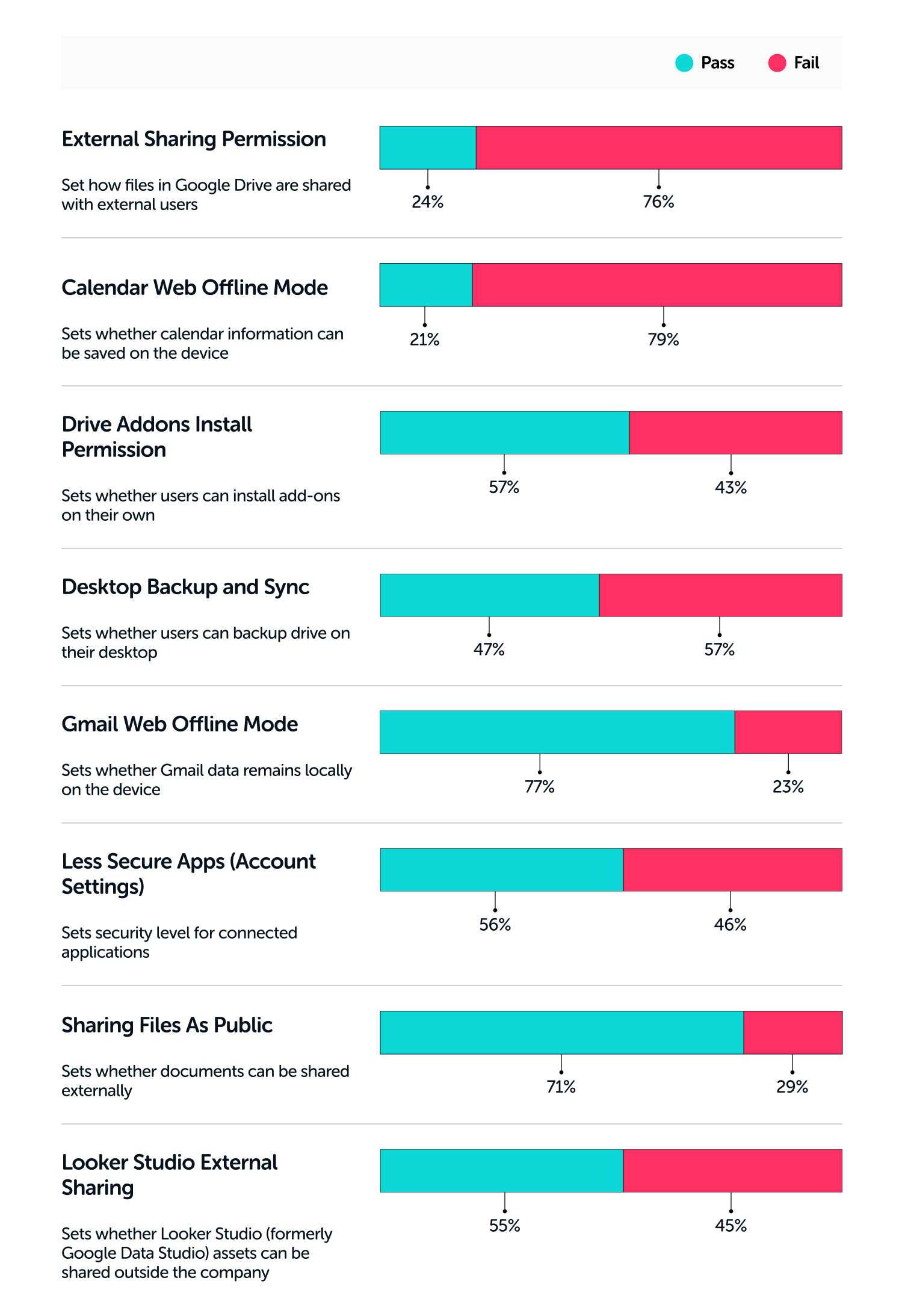
Data Leakage Benchmarks for Google Workspace
Here are some Google Workspace benchmarks to measure your settings against.
How to Prevent Data Leakage
Data leakage is a serious problem facing organizations using SaaS applications. Users often want reduced friction when sharing files with external parties, but that reduced friction can expose company secrets to others.
Security teams can better secure company documents by:
- Eliminating the ability to save files on local computers
- Require login and expiration dates on shared files
- Enforce external sharing policy through settings
Up next in our Benchmark for SaaS Apps Series is Malware Protection.